使用OP快捷运维系统waf功能
操作步骤,先使用https://opcache.com/doc/post-1/安装后
- 1.opclient开启上传waf日志和拦截功能
mkdir -p /data/nginx-log/waflogs/
touch /data/nginx-log/waflogs/waf.log
chmod 777 /data/nginx-log/waflogs/waf.log
cat /opt/opclient/config/config.toml
http-port = 8081
[config]
project-secret = "7757858585ec950f214b6868787gtyy"
project-name = "test"
data-path = "data"
waf-log-path = "/data/nginx-log/waflogs/waf.log"
nginx-path = "/opt/sh/nginx.sh"
nginx-shell-path = "/opt/sh/nginx.sh"
waf-log-enable = "false"
intercept-enable = "false"
##log-format
intercept-duration = "10"
server-url = "http://127.0.0.1:8080"
client-id = "212"
- 2.修改这两项配置waf-log-enable = “true"和intercept-enable = “true”
http-port = 8081
[config]
project-secret = "7757858585ec950f214b6868787gtyy"
project-name = "test"
data-path = "data"
waf-log-path = "/data/nginx-log/waflogs/waf.log"
nginx-path = "/opt/sh/nginx.sh"
nginx-shell-path = "/opt/sh/nginx.sh"
waf-log-enable = "true"
intercept-enable = "true"
##log-format
intercept-duration = "10"
server-url = "http://127.0.0.1:8080"
client-id = "212"
- 3.重启opclient进程生效
cd /opt/opclient
bash start.sh restart
-
4.验证攻击是否拦截,浏览器访问 http://xxx.xxx.xx.xx/?aaa=select%20*%20from%20sfsdf;
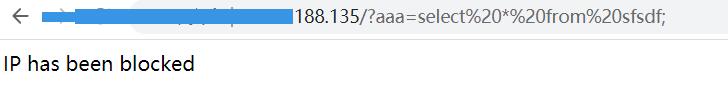
-
5.OP快捷运维系统,拦截日志中会出现攻击日志记录
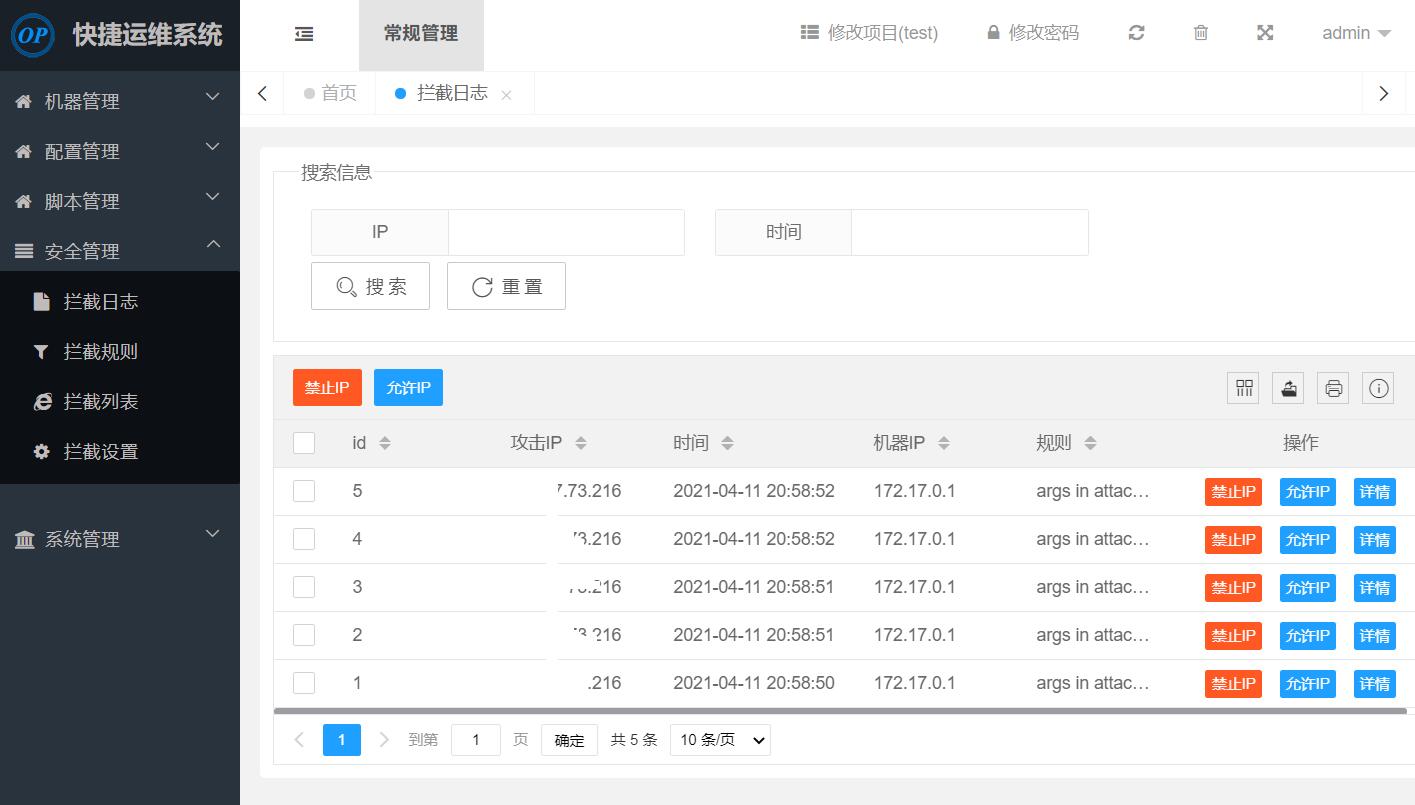
-
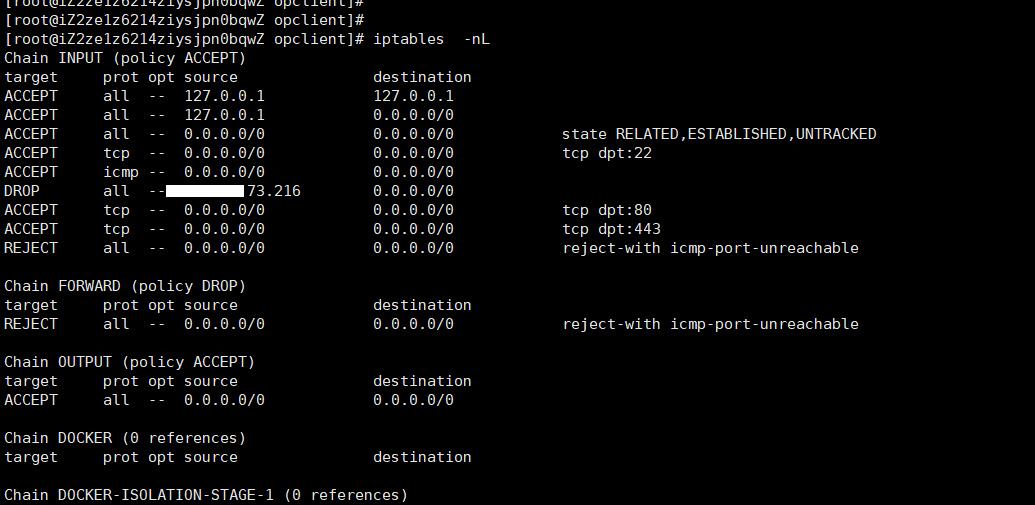
6.服务器系统里面使用iptables -nL命令,可以看到攻击IP已经drop掉